Resource
Overview
The Resources feature empowers product security leaders to identify, map, classify, and prioritize critical resources within complex cloud environments. The term "Resources" refers to individual code repositories. Soon, Resources will include cloud services as well.
By leveraging Jit's Context Engine, Resources provides a comprehensive view of all code repositories and cloud services, helping you focus remediation efforts on the assets that matter most.
The Resource Dashboard
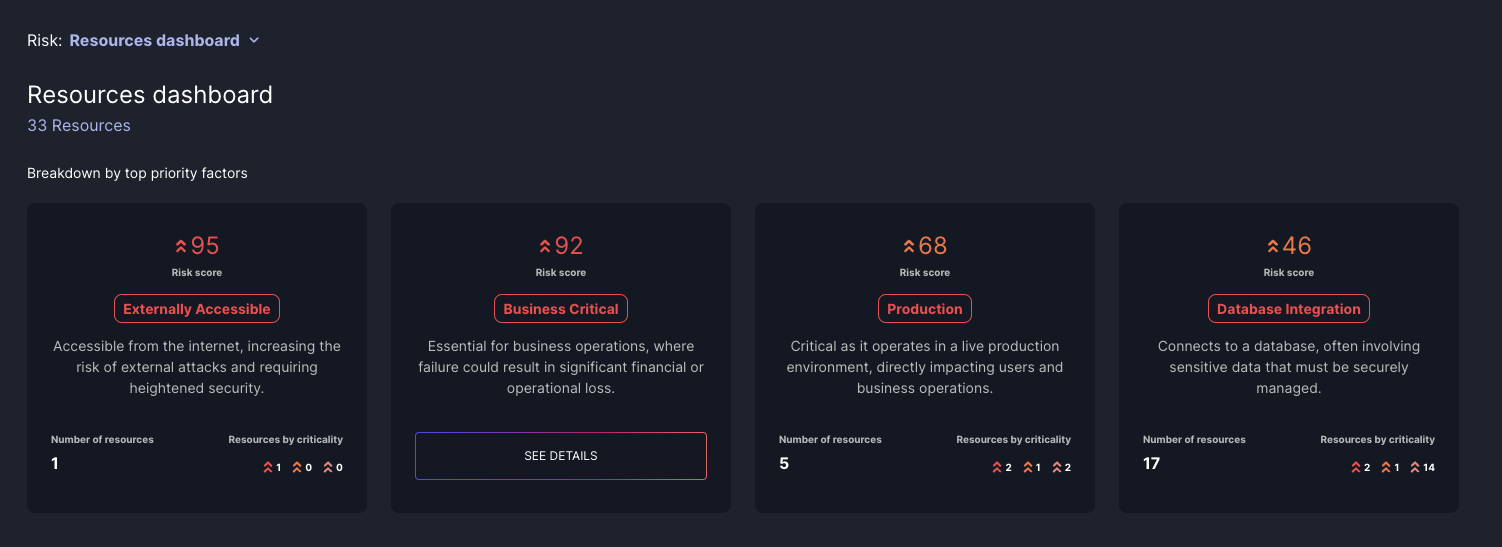
The Resource Dashboard is the first screen you encounter accessing the Resources feature. It offers a high-level summary of your resources, grouped by key Priority Factors influencing their criticality.
Key Components
Priority Factor Tiles
Priority Factors are characteristics of a resource that impact the priority of security issues that reside within it. At the top of the dashboard, you'll see tiles representing different priority factors such as:
- Production Environment: consolidates all resources within your production environment
- Internet-Facing: consolidates all resources that are externally accessible via the internet
- Database Access: consolidates all resources that have access to a database
- Business-Critical Service: consolidates all business-critical services, which are manually tagged
Tag Group Tiles
Below the Priority Factor tiles on the Resource Dashboard, you'll find tiles that refer to specific tag groups. These tiles represent custom tags that you have assigned to your resources. Manual tags allow you to group resources based on criteria that are most relevant to your organization, such as specific applications, teams, microservices, or any other categorization you choose.
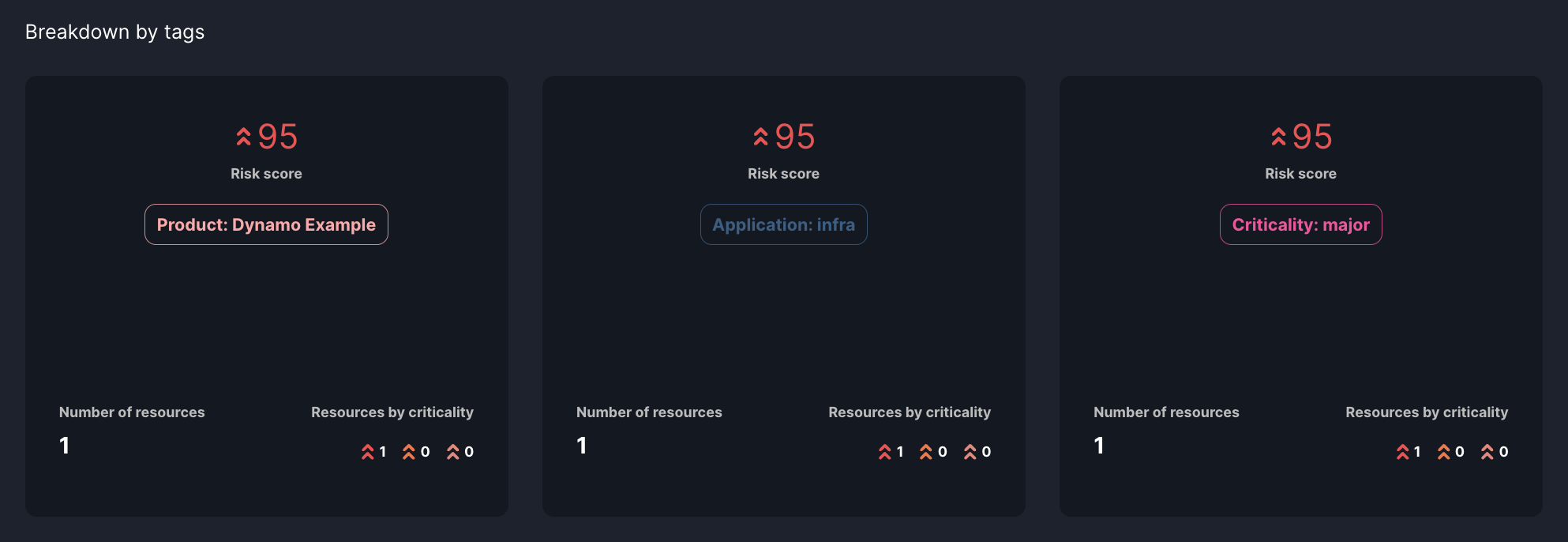
Each tile displays the number of resources that fall under that specific priority factor and the aggregated risk score for resources within each priority factor or tag, helping you quickly identify areas of concern.
Click on any tile to view resources associated with that priority factor or tag.
Link to all resources
Above the priority factor tiles, there's a link to see all resources. Clicking this button lets you view a comprehensive list of all your resources, regardless of their associated priority factors.
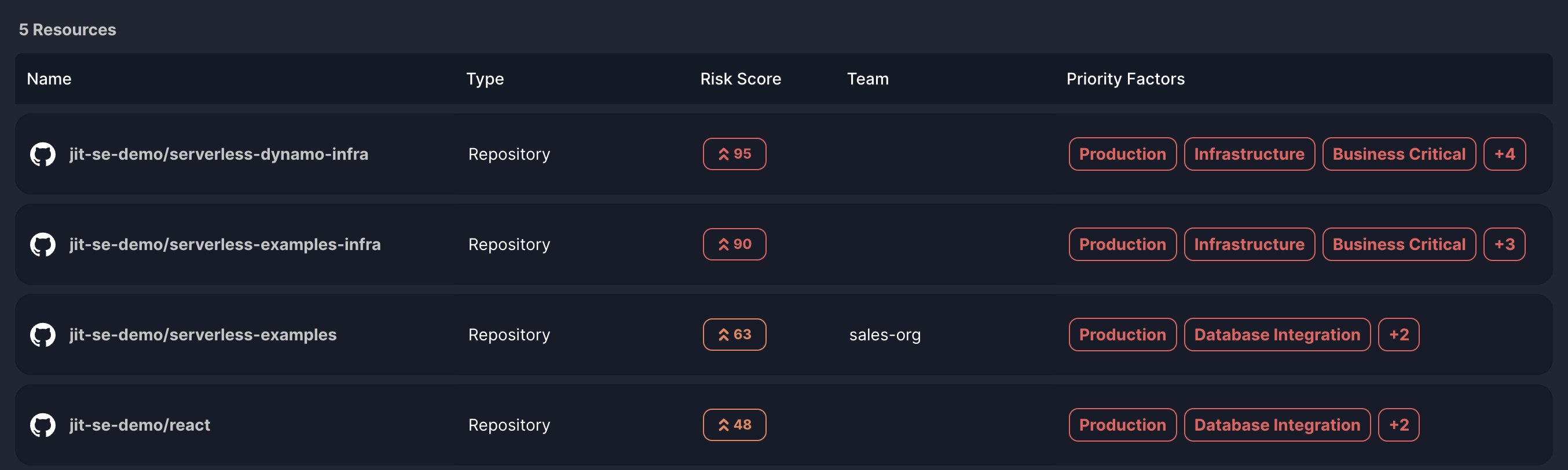
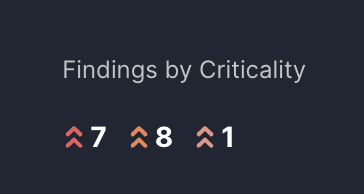
The Resource Table
After selecting a priority factor or clicking the 'All Resources' button from the dashboard, you're taken to the Resource Table. This screen lists all relevant resources, providing detailed information to help you assess and prioritize each one.
Key Components
Resource Table
A tabulated list of resources with the following columns:
| Column | Description | Example |
|---|---|---|
| Name | The name of the code repository or cloud service. | jit/react |
| Type | code repository or cloud service. | Repository |
| Risk Score | The numerical score represents the resource's criticality based on unresolved security issues and priority factors created by the context engine. | 85 |
| Team | The team that is responsible for the repository. | The A-team |
| Priority Factors | Labels indicating which priority factors apply to each resource. | Production |
Sorting and Filtering
Options to sort resources by the table properties.
Link to all associated findings
When you click the link to the Backlog on the top right corner of the screen, it is filtered to display only the findings associated with the resources in your current view. This also presents the distribution of the criticalities of these findings. For example, if the Resource Table is filtered to show only resources with the priority factor "Production", the link will lead to a Backlog view displaying only the findings found on production resources.
The Resource Page
Clicking on a specific resource from the Resource Table takes you to the Resource Page, which provides an in-depth view of the selected resource, including its connections, security issues, and detailed properties.
Key Components
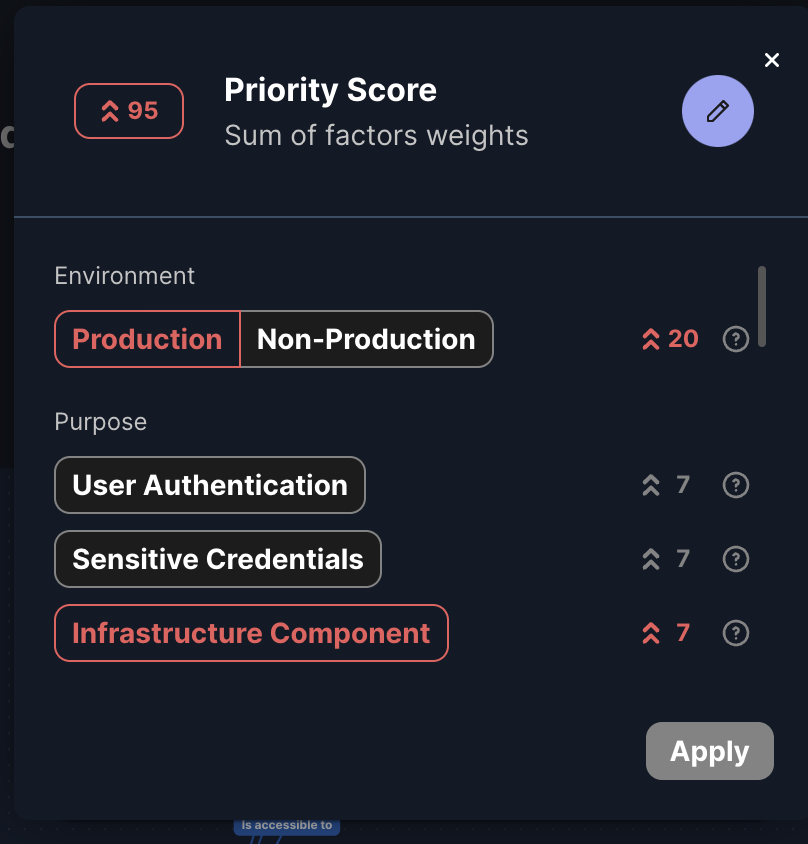
Priority Factors and Risk Score
At the top, the resource is labeled with its priority factors, such as "Production Environment" or "Externally Accessible," indicating why it's critical. The risk score is calculated by summing the weights of each assigned priority factor, reflecting the resource's overall criticality.

You can manually adjust the priority factors to accurately represent the resource's importance. Once you change a priority factor, it will affect the priority of the resource and its associated findings from that point forward, making it a reliable way to preserve and maintain accurate information about your assets.
Manual tags
On the Resource Page, you can view and manage the manual tags assigned to the resource. These tags appear alongside priority factors at the top of the page. You can add or remove tags to accurately reflect the resource's role within your environment.
To assign new manual tags to the resource, click on the 'Add Tag' button. Tags are created using a key-value structure, where the key determines the type or category of the tag, and the value specifies the name or identifier. For example, you can use Key: Application, Value: Payment to tag a resource associated with the Payment application.
Adjusting manual tags updates how the resource is grouped in the Resource Dashboard and affects the aggregation of risk scores in the corresponding manual tag tiles.
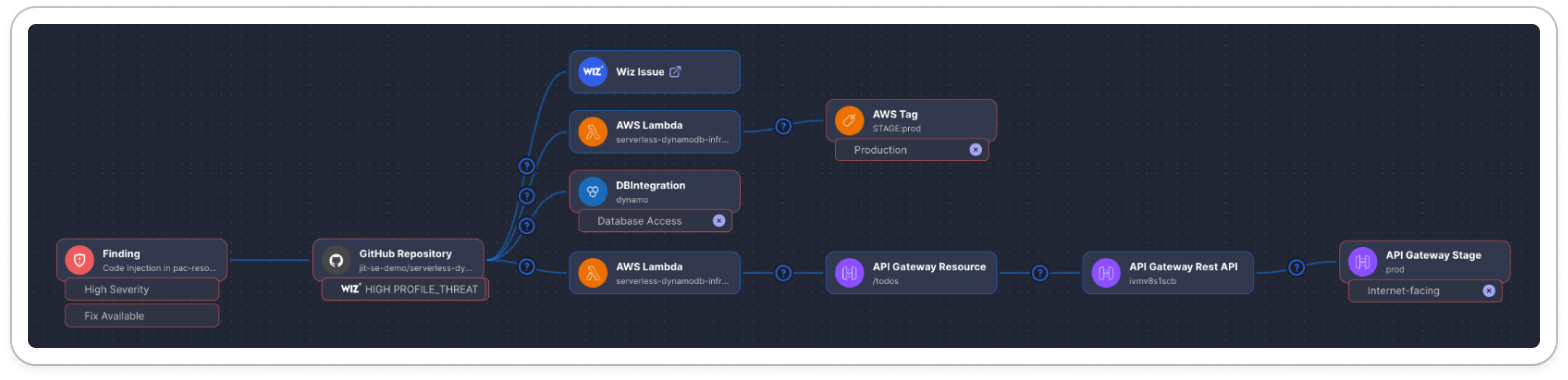
Context engine graph
Below the risk score, the Context Engine Graph visually maps how the resource connects to other elements in your environment. This visualization helps you understand relationships and potential impact pathways, illustrating how vulnerabilities might propagate. Importantly, the graph can be used as a justification or explanation of how the priority factors were concluded. By examining the connections and dependencies shown in the graph, you can see why certain priority factors apply to the resource based on its interactions within your environment.
Findings
Further down, the Findings section lists all unresolved security issues associated with the resource. Each finding includes details like the issue name, severity, type, and detection date, allowing you to assess vulnerabilities and plan remediation steps.
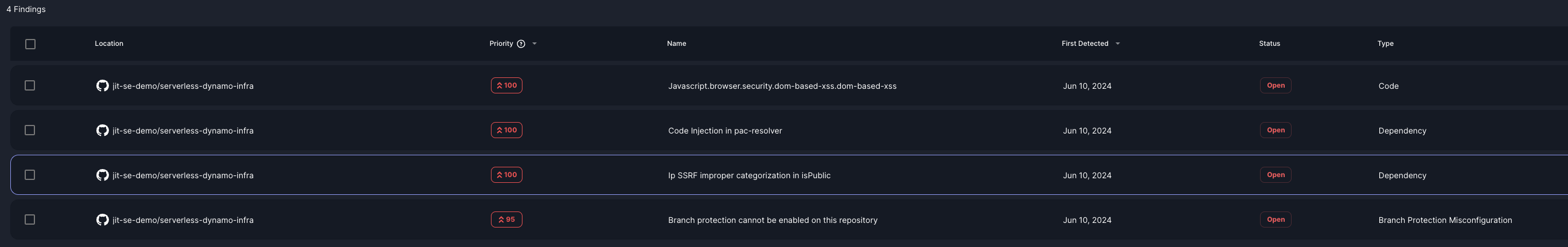
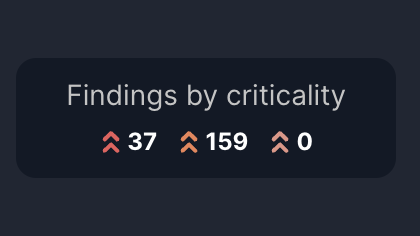
Findings by criticality
At the top-right corner, a summary categorizes the findings by their severity levels—Critical, High, and Medium/Low. This breakdown helps you understand the distribution of severities among the findings for this asset
Updated about 1 month ago
