Security Mapping
Security Mapping is based on DevSecOps philosophy, which creates a work culture where everyone is responsible for security and security is not seen as a barrier to the software development and deployment process.
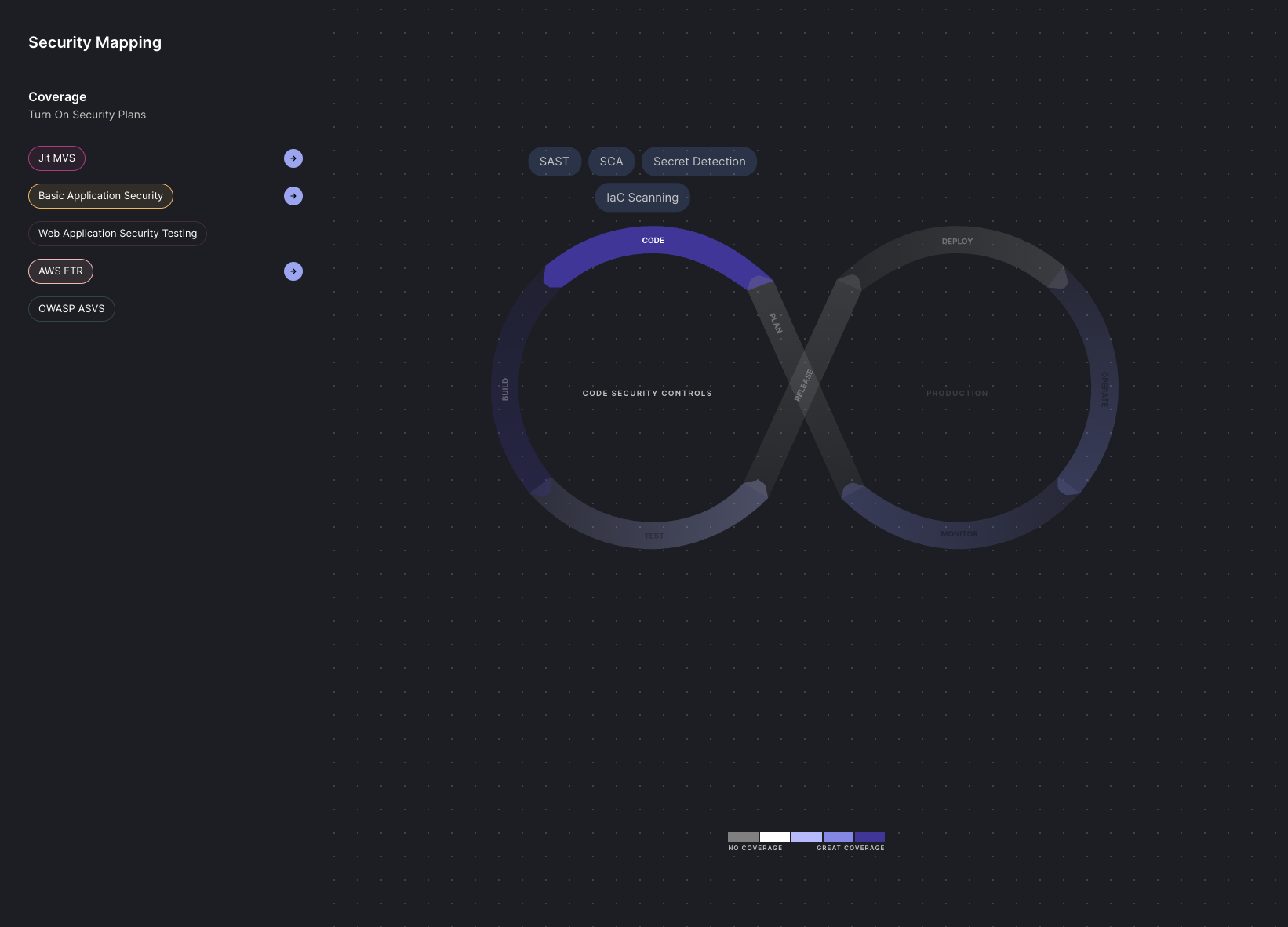
Set in an interactive interface, Security Mapping displays the full software delivery lifecycle of your organization together with the security controls you need to activate to project your code throughout each stage. For increased usability, the lifecycle of each Security Plan is color-coded where the color increases to match the level of protection provided.
Working in Security Mapping
-
Go to the left panel and select Security Mapping.

Field Description Coverage Displays a list of available Jit Security Plans. Plans are color-coded. An arrow is displayed adjacent to a selected plan. Left side Pre-production stages from Plan, Code, Build, Test to Release. Right side Production stages from Deploy, Generate, Monitor to Release. -
Click a Security Plan to display its coverage. Darker colors indicate increased security coverage.

-
Hover over a stage to display the selected security plan's security controls.
-
To go to a security plan, select the plan and click the adjacent arrow.
Software development lifecycle stages
| Stage | Description |
|---|---|
| Plan | Encompasses critical activities like project management planning, system architecture & design, formulating test strategies, and crafting a security approach. |
| Code | Jit integrates code scanning tools which are triggered by pre-commit hooks and in Pull Requests. This helps developers to identify and remediate security issues early, significantly reducing the risk of vulnerabilities later on. It also educates developers about secure coding practices, enhancing overall code quality. |
| Build | Jit employs code security tools that are activated both when new code is merged to the codebase and on a scheduled basis. This approach ensures comprehensive scanning of all existing code, promptly identifying and addressing any security vulnerabilities as they emerge. |
| Test | To detect and mitigate runtime vulnerabilities that are only observable when the application is running, Jit triggers DAST and CSPM tools for real-time testing of the application in a near-production setting. |
| Release | Software artifacts are digitally signed to certify that they have successfully passed the build process, all testing stages, and security scans. This step is used for verifying the integrity and security of the software before it is deployed, ensuring that what reaches the production environment hasn't been altered. |
| Deployment | Jit triggers DAST and CSPM tools to the production environment, thoroughly testing the application in its final, operational state.This ensures that potential security vulnerabilities are identified in the production environment immediately after the application is deployed, minimizing the time to detection and remediation of vulnerabilities. |
| Operate | DAST and CSPM tools run on a scheduled-basis, continuously monitoring the security posture of the application in the production environment to identify and respond to security vulnerabilities or threats, ensuring ongoing protection of the application in runtime. |
| Monitor | Jit continuously monitors and assesses the security posture of the application and infrastructure and helps identify any issues or areas that require improvement. It aids in the implementation of a vulnerability management process, which guides necessary actions in subsequent iterations. |
Updated 12 months ago
