GCP Integration
Integrating with GCP
Google Cloud Platform integration enables you to scan your GCP infrastructure for runtime misconfigurations. Though it does not require the integration steps below, Jit recommends that you also activate the Scan IaC for Misconfigurations security requirement for complete infrastructure protection.
Two Integration Methods
You can connect your GCP project to Jit using one of two supported approaches:
Option 1 (Recommended): Using Workload Identity Federation (WIF)
This is the preferred and more secure method. It avoids storing static credentials by leveraging federation from AWS (e.g., Lambda, EC2, Fargate) to impersonate a GCP Service Account.
Option 2: Using a GCP Service Account (Key File)
This is the traditional and simplest method. It uses static JSON key for the service account to authenticate.
ℹ️ Navigate to Jit → Integrations and select the GCP card to begin setup
Before You Start
To integrate with GCP, you'll need:
- A GCP project with billing enabled. This ensures all required APIs function correctly—even free-tier ones.
- IAM permissions to create service accounts.
- For Option 1 (WIF): Additional IAM permissions to create Workload Identity Pools.
Shared Setup
These steps apply to both integration methods:
-
Create a new service account in your Google Cloud project. See Google Cloud documentation for details.
-
Ensure the following roles are assigned to the service account:
- Viewer
- Security Reviewer
- Stackdriver Account Viewer
ℹ️ Jit will only scan GCP projects where the service account or federated identity has been granted access.
-
Make sure the Google Cloud Resource Manager API is enabled on the account.
Detailed Setup Instructions
Option 1 (Recommended): Using Workload Identity Federation (WIF)
Steps:
-
Create a new Workload Identity Pool in your GCP project to enable federation from JIT. See instructions to create a Workload Identity Pool for instructions.
-
Create a new AWS provider within that pool.
-
Get the JIT AWS Account ID: Go to Jit → Integrations → GCP and start the integration setup. The required AWS Account ID will be displayed in the integration modal. Copy this Account ID - you'll need it for the next step.
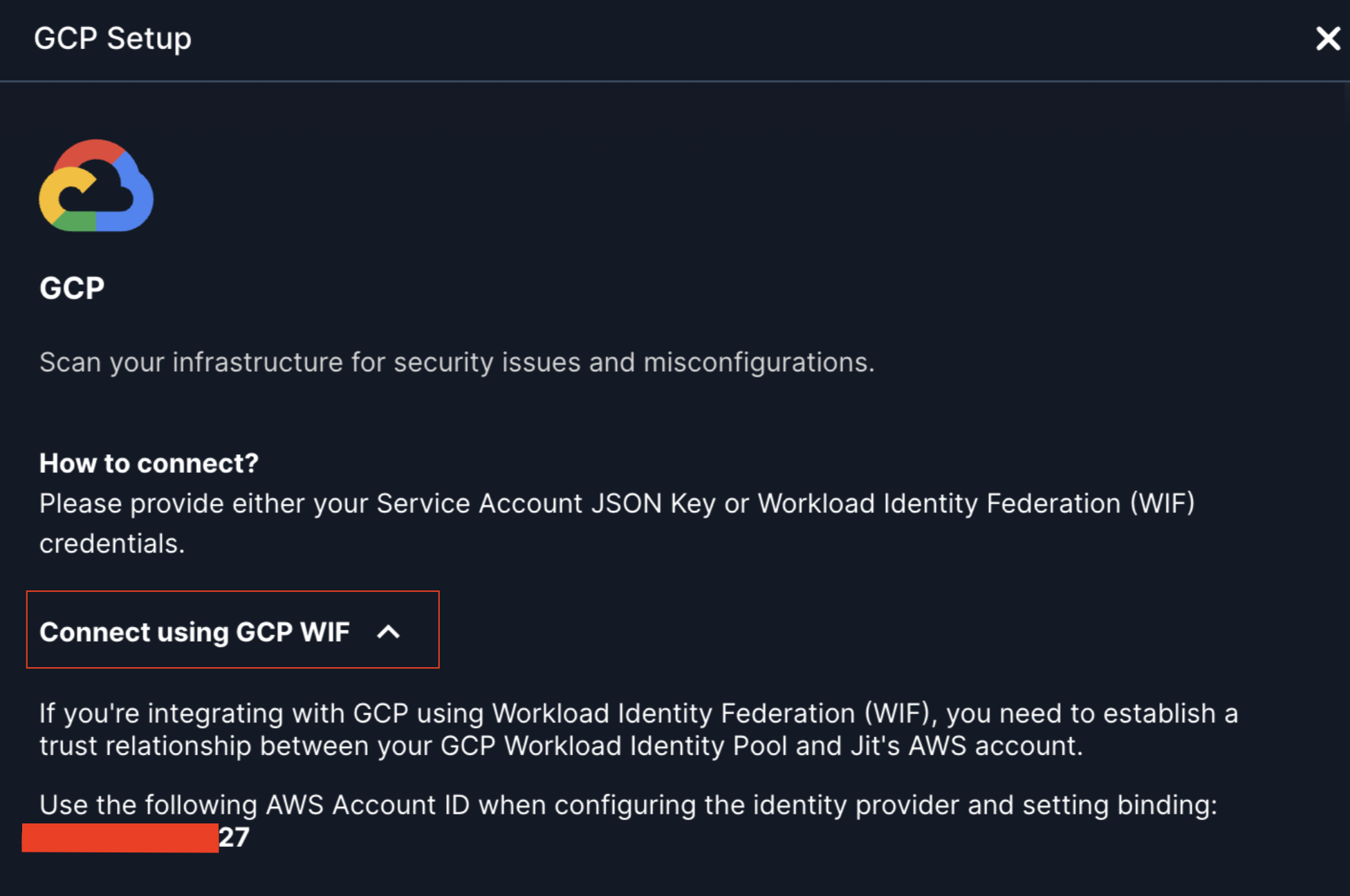
-
Bind the
roles/iam.workloadIdentityUserrole to all identities from your JIT AWS account so they can impersonate the service account. See Google Cloud documentation. Use the AWS Account ID from the previous step. -
Create WIF file that enables JIT workloads to authenticate with GCP using the created provider. Use this command.
⚠️ This file is a WIF credential configuration, not a service account key. It contains no secrets and enables token exchange from AWS.
Example WIF Credential Configuration File
{
"type": "external_account",
"audience": "//iam.googleapis.com/projects/123456789/locations/global/workloadIdentityPools/my-pool/providers/my-provider",
"subject_token_type": "urn:ietf:params:aws:token-type:aws4_request",
"token_url": "https://sts.googleapis.com/v1/token",
"credential_source": {
"environment_id": "aws1",
"region_url": "http://169.254.169.254/latest/meta-data/placement/region",
"url": "http://169.254.169.254/latest/meta-data/iam/security-credentials",
"regional_cred_verification_url": "https://sts.{region}.amazonaws.com?Action=GetCallerIdentity&Version=2011-06-15"
}
}
-
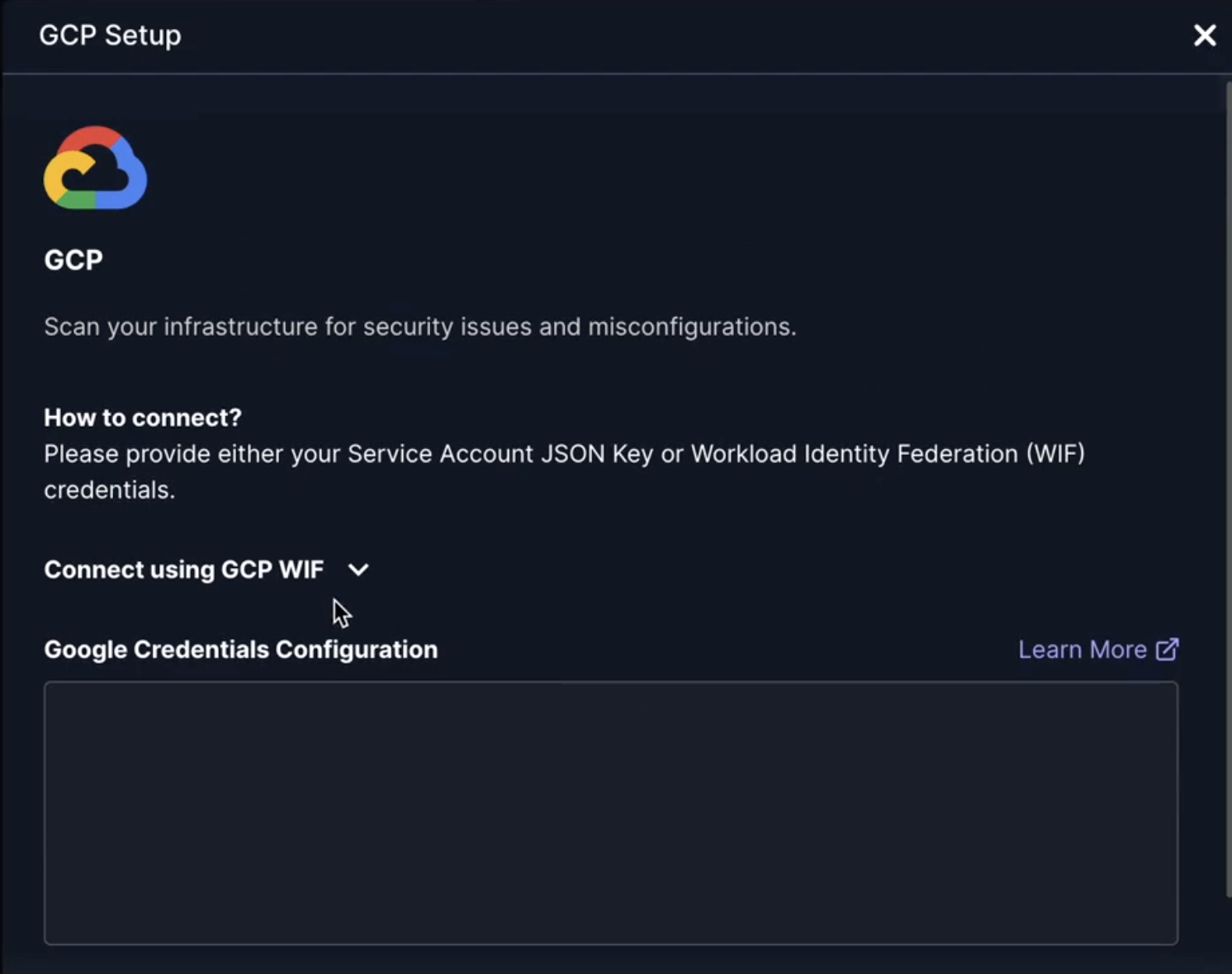
Go to Jit → Integrations → GCP and paste your WIF credential configuration.
-
Confirm connectivity in the Jit UI using the "Connect" button to validate access.
Option 2: Using a GCP Service Account (Key File)
Steps:
-
Create a new service account in your Google Cloud project. See Google Cloud documentation for instructions.
-
Go to Jit → Integrations → GCP and upload your JSON key.
-
Confirm connectivity in the Jit UI using the "Connect" button to validate access.
Integration CompleteOnce successfully connected, Jit will begin scanning your GCP infrastructure for runtime misconfigurations. The integration enables continuous monitoring of your cloud resources to identify security vulnerabilities and compliance issues across your GCP projects.
Managing Your IntegrationDisconnecting from GCPTo disconnect your GCP integration:
- Go to Jit → Integrations → GCP
- Click on the connected GCP card
- Select "Disconnect" to remove the integration
Updated about 1 month ago
