Splunk Integration
Jit's integration with Splunk Cloud makes it easy to stream your audit logs to Splunk for storage and analysis using Splunk's event collector.
You can learn more about Jit's audit logs here.
Quickstart
-
In Jit's web app, go to the Integrations page.
-
Find the "Splunk Cloud" card and click "Connect".
-
You should now see a Splunk integration window. Click on "Connect" at the top right corner.
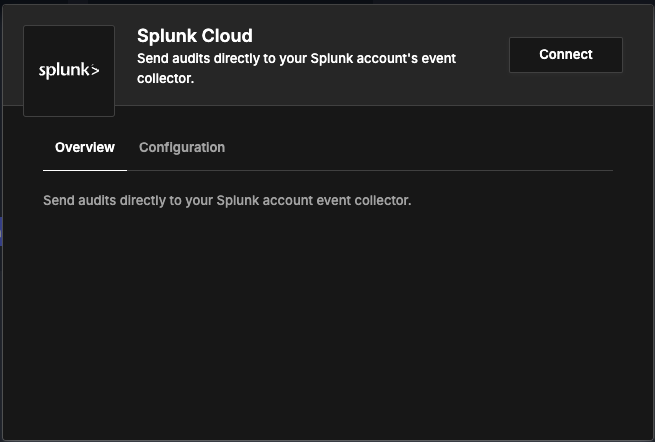
-
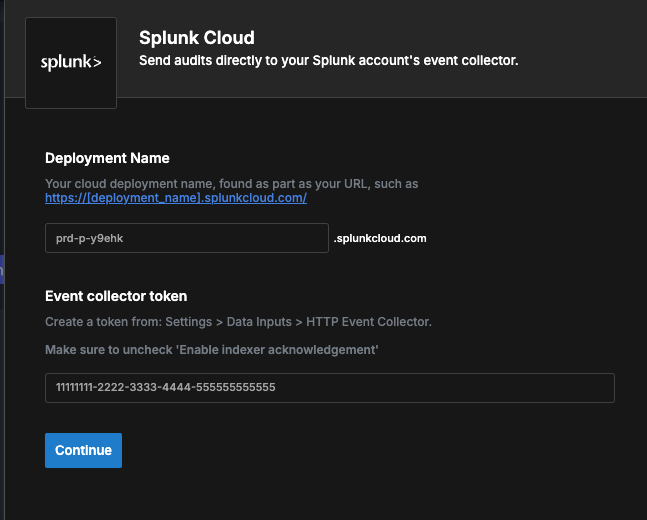
You will now need to provide your deployment name (from your splunk URL) and the HTTP Event Collector (HEC) token that will be used to send events.
-
Log into your Splunk Cloud account.
-
Navigate to Settings > Data Inputs
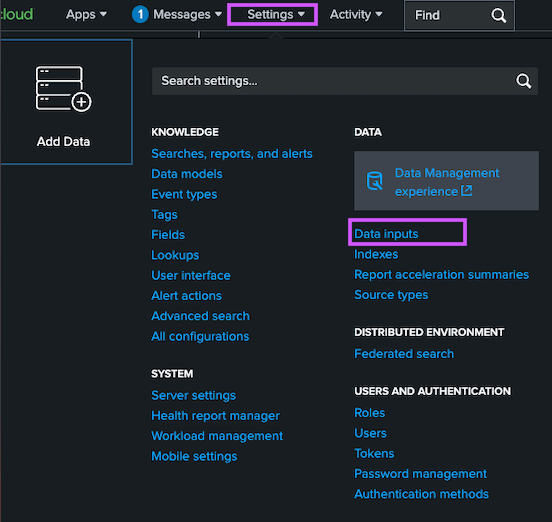
- Under Local Inputs, HTTP Event Collector click Add new
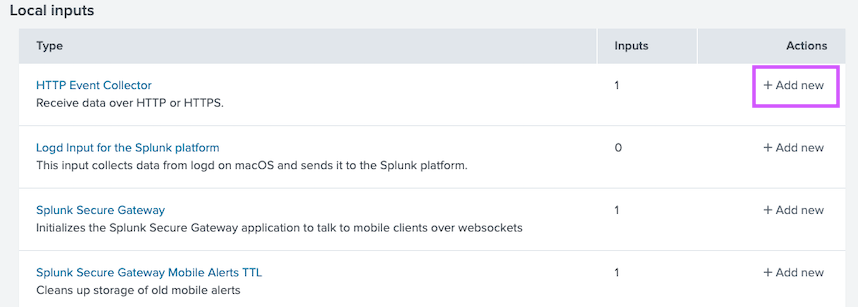
-
Follow these steps:
-
Name your token (e.g., "Jit Integration").
-
Make sure
Enable indexer acknowledgementis Unchecked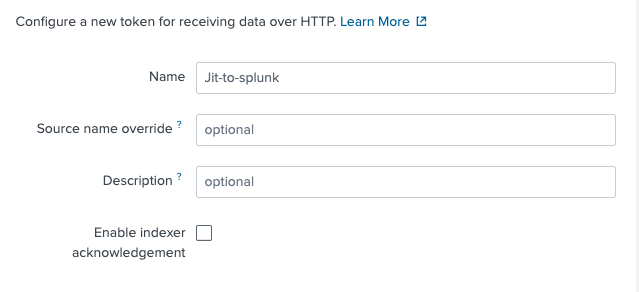
-
-
Click Next
-
Choose the indexes that will ingest Jit's audit logs (under
Selected items(s))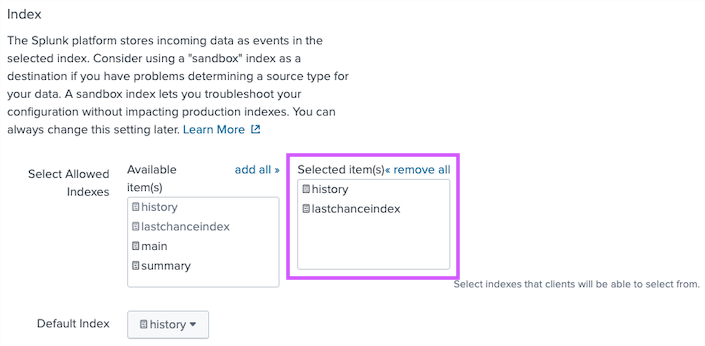
-
Click Review -> Submit and copy the generated token. Please note that if the token is deleted or modified, events from Jit will no longer be logged to Splunk Cloud.
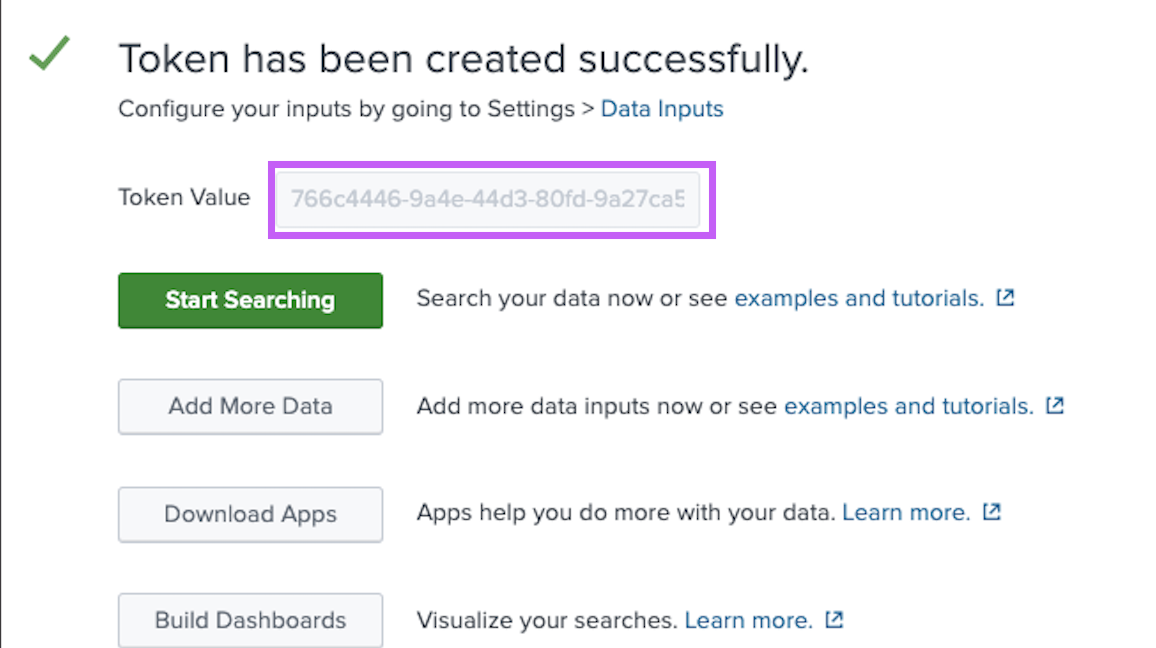
Learn more in Splunk documentation.
-
-
Paste the token in the "Event collector token" textbox and click Continue.
If the token is valid, your integration is now active, and you can begin ingesting audits to your instance.
-
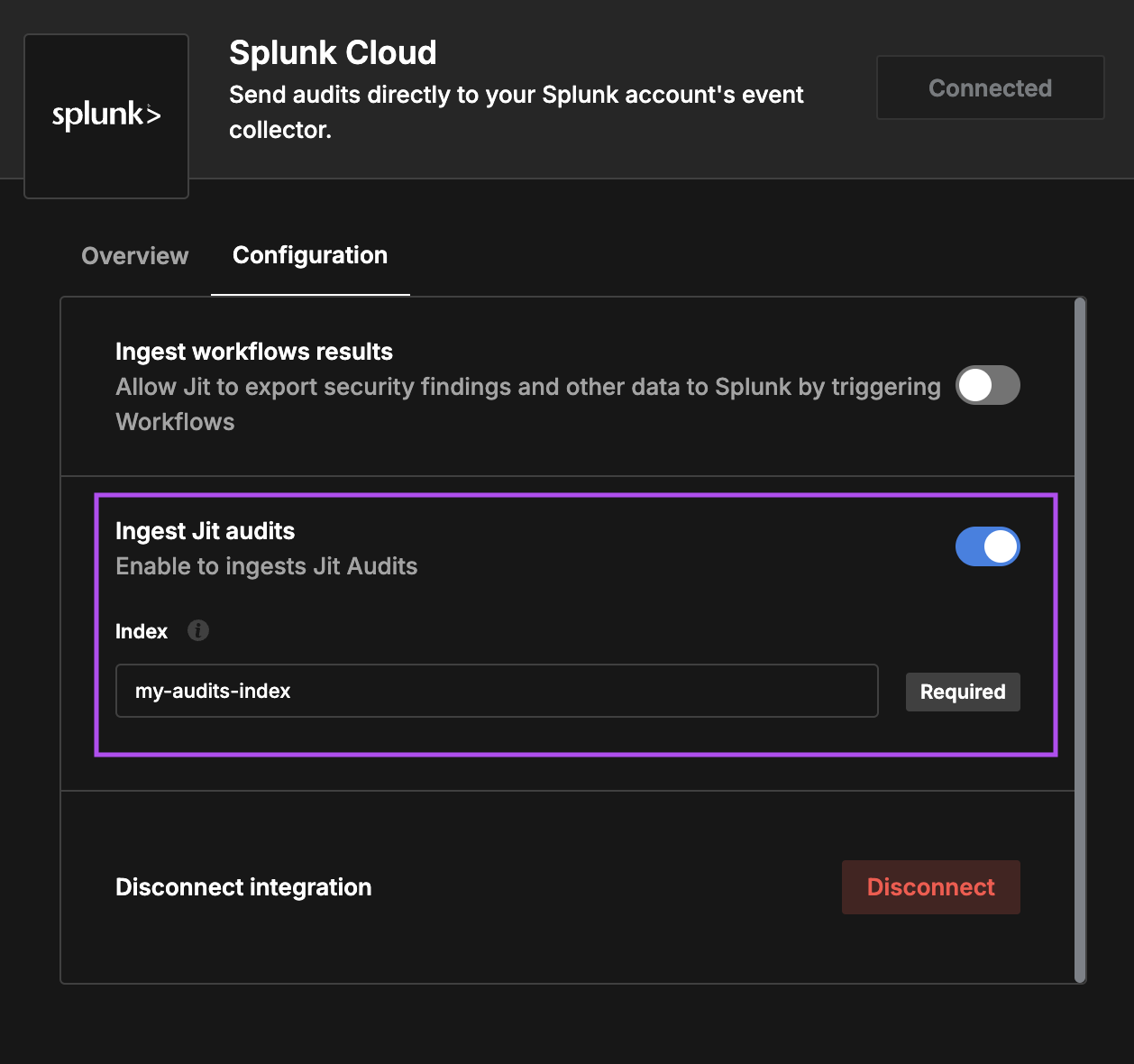
Enable audits ingest, and select the desired index. The index must be included in your token configuration.
Sample event
{
"severity":"Info",
"action":"Export plan results",
"description":"Export Plan Test Plan results",
"userAgent":"Mozilla/5.0",
"ip":"192.168.0.1",
"email":"[email protected]",
"plan_name":"Test Plan"
}
Ingesting findings and other data through Jit Workflows
-
First, enable the
Ingest workflows resultsin order to activate it. You may choose different index from the audits one.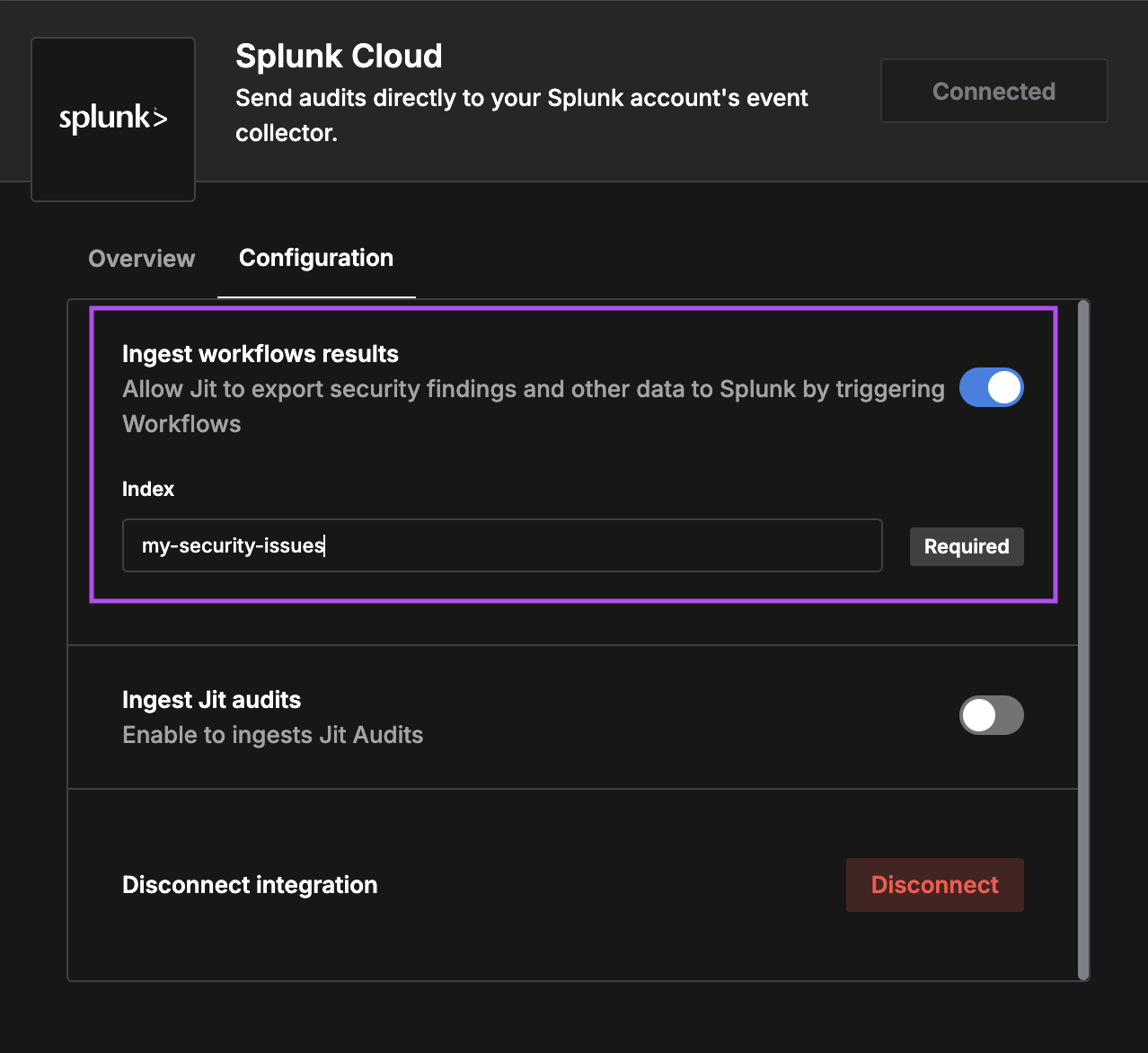
-
You can now use splunk as a target in your workflows
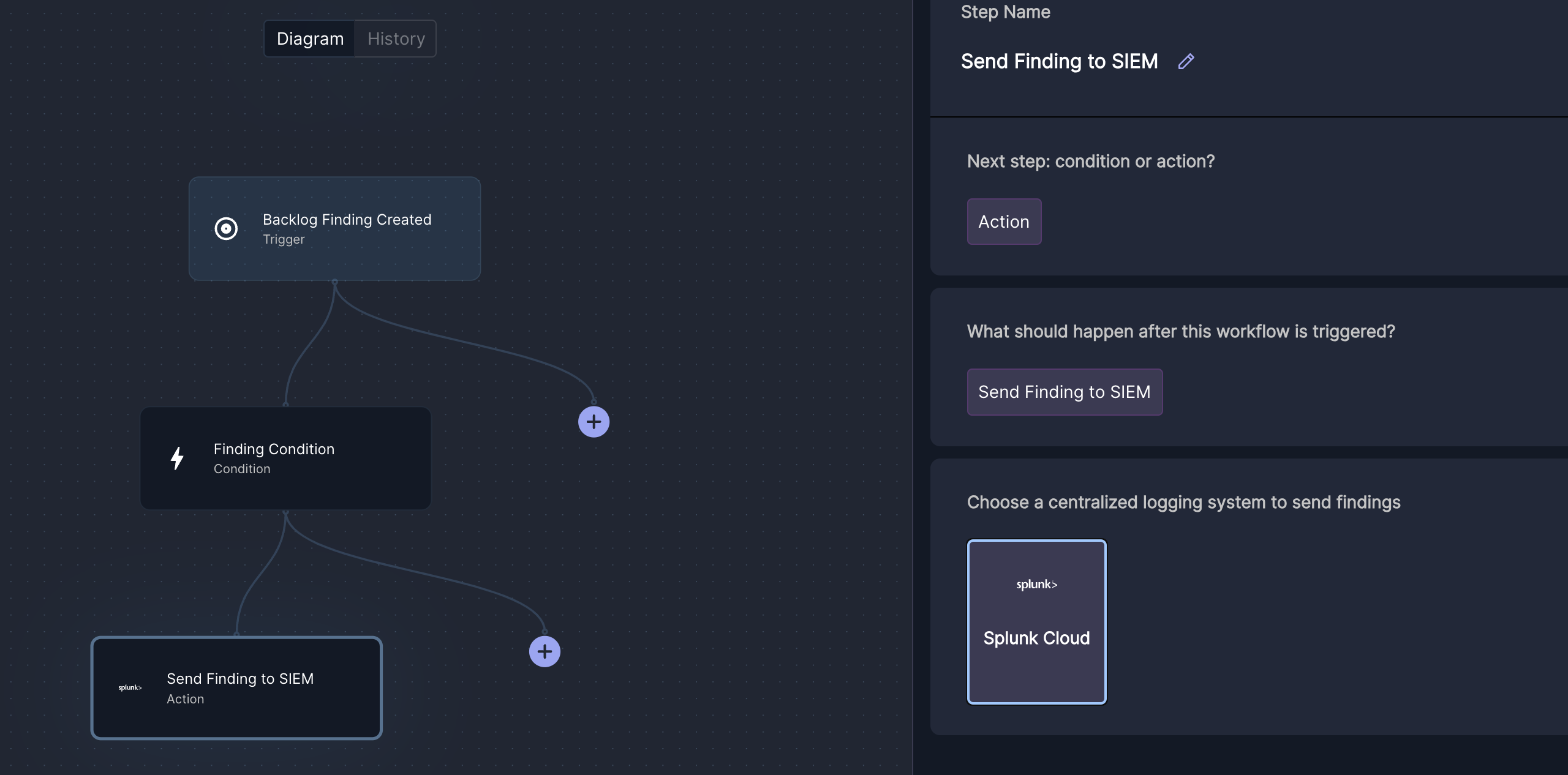
Sample event
{
"id": "11111111-2222-3333-4444-555555555555",
"status": "PASS",
"tenant_id": "aaaaaaa-bbbb-cccc-dddd-eeeeeeeeeeee",
"asset_id": "ffffffff-gggg-hhhh-iiii-jjjjjjjjjjjj",
"asset_type": "repo",
"asset_name": "SampleRepo",
"asset_domain": "TestProject",
"workflow_suite_id": "kkkkkkkk-llll-mmmm-nnnn-oooooooooooo",
"workflow_id": "pppppppp-qqqq-rrrr-ssss-tttttttttttt",
"first_workflow_suite_id": "kkkkkkkk-llll-mmmm-nnnn-oooooooooooo",
"first_workflow_id": "pppppppp-qqqq-rrrr-ssss-tttttttttttt",
"jit_event_id": "uuuuuuuu-vvvv-wwww-xxxx-yyyyyyyyyyyy",
"jit_event_name": "merge_default_branch",
"first_jit_event_name": "merge_default_branch",
"execution_id": "zzzzzzzz-aaaa-bbbb-cccc-dddddddddddd",
"fixed_at_jit_event_id": null,
"fixed_at_execution_id": null,
"job_name": "static-code-analysis-python-semgrep",
"vendor": "github",
"responsible": null,
"control_name": "semgrep",
"test_name": "Unsafe system call with risk of command injection",
"fingerprint": "1234567890abcdef1234567890abcdef1234567890abcdef1234567890abcdef",
"test_id": "python.lang.security.audit.dangerous-system-call.dangerous-system-call",
"issue_text": "Found dynamic content used in a system call. This is dangerous if external data can reach this function call because it allows a malicious actor to execute commands. Use the 'subprocess' module instead, which is easier to use without accidentally exposing a command injection vulnerability.",
"issue_confidence": "UNDEFINED",
"issue_severity": "HIGH",
"plan_layer": "code",
"vulnerability_type": "code_vulnerability",
"cwes": [
"CWE-78"
],
"cves": null,
"resolution": "IGNORED",
"references": [
{
"name": "https://semgrep.dev/r/python.lang.security.audit.dangerous-system-call.dangerous-system-call",
"url": "https://semgrep.dev/r/python.lang.security.audit.dangerous-system-call.dangerous-system-call"
}
],
"location": "https://github.com/TestProject/SampleRepo/blob/abcdef1234567890abcdef1234567890abcdef12/sample.py#L218-L218",
"location_text": "TestProject/SampleRepo",
"code_attributes": {
"branch": "main",
"pr_number": null,
"filename": "sample.py",
"line_range": "218-218",
"code_snippet": "requires login",
"head_sha": "abcdef1234567890abcdef1234567890abcdef12",
"base_sha": "",
"last_head_sha": "abcdef1234567890abcdef1234567890abcdef12",
"user_vendor_id": "987654321",
"user_vendor_username": "SampleUser"
},
"cloud_attributes": null,
"app_attributes": null,
"created_at": "2025-02-12T13:20:00.741995",
"ended_at": null,
"modified_at": "2025-02-12T15:49:15.165855",
"last_detected_at": "2025-02-12T13:20:00.741995",
"fix_suggestion": {
"guidelines": "The auto-remediation feature will replace uses of os.system with subprocess.run in the vulnerable code, ensuring a safer way of executing system commands. The vulnerability will be fixed by changing the command execution method and adapting the command input format.",
"title": "Avoid using os.system for executing system commands",
"reason": "Using os.system to execute system commands can lead to command injection vulnerabilities if user-supplied data is not properly sanitized. It is recommended to use the subprocess module for executing system commands, as it provides a more secure interface and avoids potential security risks associated with command injection.",
"source": "ai",
"filename": "sample.py",
"start_line": 218,
"end_line": 218,
"current_text": " os.system(command)",
"new_text": " subprocess.run(command, shell=False, check=True, text=True)",
"is_outside_of_pr_diff": false
},
"backlog": true,
"ignore_rules_ids": [
"bbbbbbbb-cccc-dddd-eeee-ffffffffffff"
],
"ignored": true,
"tags": [],
"priority_factors": [],
"priority_score": 0,
"priority_context": null,
"original_priority_factors": [],
"original_priority_context": null,
"manual_factors": {
"added": [],
"removed": []
},
"asset_priority_score": 0,
"filename": "sample.py",
"jobs": [
{
"workflow_slug": "workflow-sast",
"job_name": "static-code-analysis-python-semgrep"
}
],
"scan_scope": {
"language": "python",
"branch": "main",
"filepath": "sample.py"
},
"plan_items": [
"item-code-vulnerability"
],
"tickets": [],
"fix_pr_url": null,
"teams": []
}
Notes
-
Ensure that the Splunk HEC endpoint is accessible from Jit.
-
If the token is invalid or the endpoint is inaccessible, You will have to re-integrate.
Updated about 1 year ago
